they were all owned by the same company and sold to Kape, which has ties to the Israeli intelligence service, a few years back.
The issue is who he sold it to -- the notorious creator of some pernicious data-huffing ad-ware, Crossrider. The UK-based company was cofounded by an ex-Israeli surveillance agent and a billionaire previously convicted of insider trading who was later named in the Panama Papers. It produced software which previously allowed third-party developers to hijack users' browsers via malware injection, redirect traffic to advertisers and slurp up private data.
I personally use perfect-privacy, which didn't turn up any red flags when I did research a few years ago. it's a little lacking in features but openvpn isn't that hard to set up on linux & android. no clue how well their desktop app works.
glad to see another fan of the "it all has backdoors, but opposing governenments can do a lot less harm with it" approach to cybersecurity
ha jokes on them I have an inbox rule to forward everything to
support@kremlin.ru
Westerners don’t want to admit this, but the only safe VPNs are made by their enemies lol. And this isn’t even “tankie” propaganda. If you were Russian or Chinese it’d be your best interest to use western VPNs. Maybe not American ones unless you want to end up like burned Iranian CIA assets
Kaspersky was at least at one point a resold version of hotspot.
here’s an article that has a lot of details.
Hotspot isn’t exactly in the best situation to be a vpn you’d trust if you were worried about law enforcement.
That’s a good way to evaluate lots of stuff.
One way that kaspersky might not be safe enough for you, if it’s still a rebrand of hotspot which I haven’t confirmed, is that hotspot has offices in states where they can be compelled to install equipment and software to monitor throughput without notifying customers. That’s no big deal for Russians and Syrians because they’re still protected from those states actions by a bunch of layers of international law and whatnot. If you aren’t safe from, for example, the us government because you, for example, live in the us then it might not be the protection appropriate for you and your uses.
It’s one of those circumstances where at the very least a warrant canary would be good, but would also only provide certain assurances and would rely on the users awareness to function.
Kaspersky:
Server speeds of up to 10 Gbps keep your devices running fast
Does this mean I have to browse through them at 10Gbps instead of the typical 100Gbps I get from my ISP? Seems a bit painful
100gbps is insane, I think you must have your numbers wrong. Either way 10gbps is more than adequate for doing anything
Oh motherfucker PIA is the one I use
Thankfully the main reason I have it is just to steal video games but I’ll make sure that doesn’t renew
Mullvad is what I use, haven't heard of any controversies with them.
I used to use Mullvad but switched because PIA was cheaper and a looooot of sites and apps were blocking me when I used Mullvad.
Fuck you Wendys I don’t want to turn off my VPN on work wifi just to order food
Seconding Mullvad, you can send them an envelope of cash or buy a code off amazon if you really care about it that much. Technically they're in a 14 eyes country but no one here is important enough to worry about that.
The only problem is that they don't support port forwarding, so if you're a serious torrent person that can be disqualifying.
But it would seed better with port forwarding, as all VPNs would. Which is the point.
main reason I have it is just to steal video games
why do you need a VPN for that? Can you get in trouble if you don't use it?
Yeah, I’ve gotten letters from my ISP in years prior. For torrenting Silicon Valley and Gambo Thrones if I remember right
US seems to be pretty strict with it's IP laws, crazy stuff. I've seeded like a 100TB of data and never gotten anything from my ISP
in canada isps are obligated to pass on what IP holders accuse you of, but they don't actually do anything about it. the rights holders are the ones tracking torrents or whatever. i've torrented tons of music and movies and the only time i got an email was when i torrented the lady ghostbusters lol
ive heard that in the us an ISP can decide to stop providing service to you if you get too many tho
Depends on where you live, but they like to periodically make examples out of people and sue them for like half a million dollars
perfect-privacy
$120 a year, god damn. I used PIA because it was $80 for 3 years and because like 10 people can use the same account.
for others switching from PIA,
-
kaspersky is about $35 a year ($30 first year, then $45) for 5 devices
-
protonvpn $60 a year for 10 devices with the 2 year plan
-
Mullvad is $60ish a year for 5 devices (no port forwarding)
-
IVPN is $80 a year for 7 devices with 2 yr plan (no port forwarding)
I also was just looking, and that "reasonable price if you prepay for two years" nonsense is, well, nonsense. I ain't exactly looking to spend $120+ all at once while crossing my fingers in the hopes the service doesn't suck.
Kaspersky seems like a good move, the page is saying it renews at $40/yr which is only $10 more than my current provider. Only five devices is a shame, though.
I was leaving towards them too. I paid for two years of NordVPN and got a refund when it sucked ass, so I'm guessing other companies do that if it isn't great
-
There’s a significant difference between the threat model surrounding vpns that you intend to use for port forwarding torrents and vpns you intend to use to protect yourself from data harvesting/the cops.
Don’t expect one to do both.
I'm posting this here because a lot of use a VPN for organizing. this doesn't matter if all you care about is torrenting.
I totally agree. I made my post for the same reason but not in direct reply to anyone talking about torrenting.
E: the thing I’m generally posting in the direction of is that all vpns aren’t the same and just turning yours on before you click on the link while you flip down your sunglasses and say “I’m in” or even checking out a company’s reviews before you sign up isn’t enough to keep you protected in the limited ways that VPNs are able to.
I’m using a hypothetical “you” here, not trying to accuse you of those practices in a passive aggressive way.
I follow, just wanted to clarify because I didn't call it out in the post
The ideology and commitment of a service provider is irrelevant. Companies doing business in a nation are compelled by force to follow those nations laws.
I would advise against looking for an “all round” vpn. Think about it more like a tool. No one would recommend you replace a socket wrench set with a gerber multitool because the gerber has a lifetime warranty and a screwdriver and wire cutter built in. Those are great things to have and gerber really will honor that warranty when you break the pliers fucking around with barb wire but the multi tool isn’t a socket wrench.
I use a few vpns. Mullvad, air, proton and a few classic style lil servers that just handle traffic. Air and proton are both very good for torrenting and running services. Mullvad is nice for getting/being serious about privacy from states.
To use another metaphor, think about a vpn like a gun. They’re not all the same and if you try to use one to do something it’s not suited for you’ll by unsuccessful.
If you feel comfortable talking about it, what are you planning on using a vpn for?
When the police have a wiretap warrant they’ll install their own logging facilities.
If you’re really worried id setup and be prepared to use two different vpns, with multihop when the time comes. Not at the same time, but be prepared with a backup.
One of the ways that effective vpns are targeted is with websites and services blocking their servers. Mullvad had that happen last year when interpol wanted to push csam people off of it. The csam people were using port forwarding to host file sharing with the security that mullvad provided and in order to get mullvad to stop offering port forwarding they leaned on every major website to block their server ips. Whole fens wouldn’t respond to you if you were using mullvad. Eventually they stopped offering the service and the csam people had to go elsewhere.
So even an effective vpn can be targeted and it’s worth it to have a backup.
E: also those servers seized in ukrane were unencrypted, which is a huge incredibly stupid unforced error and it means they better have done a big fucker key rotation afterwards. I don’t use windscribe so I don’t know if they did.
What made you raise your eyebrows at mullvad? I know they had a search executed on em but it ended up being a big nothing burger iirc.
I wouldn’t worry about the eyes-ness of a providers operations based on your concerns. What’s most important is having a fallback for when your main vpn isn’t available and making sure you’re using the fallback when that happens.
The thing you’re worried about isn’t a particular agency targeting you in particular, but being swept up in police action and mass surveillance. To that end it doesn’t really matter as much that your vpn have the lack of interpol cooperation or even the obfuscating effect of using the same exit node as a bunch of other people but instead that you be always using one, understand what it does and who or what your devices are communicating with and practice the best possible security you can when dealing with the cops.
Look into securing your devices against intrusion (and keeping secure backups) and how to deal with the police when they take you in. For example: an iPhone is put in a special state when it’s powered on that requires strict authentication before any kind of peripheral will be recognized. If you can’t turn the phone off then just grabbing the two buttons that put it in the “slide to power off” screen drops all peripheral connections and needs an authentication before it’ll let anyone use it.
Drill that interaction so that no matter how gassed, beaten and dazzled you are, you can put your devices in some kind of secure-ish state.
I'm sure they still spy on my torrents but this is why I don't use any vendor provided apps or software for VPN shit (or anything else without a very compelling reason tbh), it's practically guaranteed to be adware or spyware
I guess it's time to check if my provider is on this list though
I don't know the situation on Windows but the network manager VPN integration on Gnome is actually pretty amazing. Just have my VPN set to auto connect and it just works and comes right back up without any drama when the system wakes from sleep or switches access appints etc. definitely +1 for not using the vendor apps.
Huh I've been using that same integration for years with ubuntu, and now pop os, and haven't seen an option to auto-connect... Not sure I'd want to anyhow for this particular device since I have a bunch of different vpns configured but wondering where you set that? Maybe it's just Pop that doesn't have that in the UI? I'm sure I can toggle it in nmcli
The old Pop! shell (I assume you're using the old one since last I checked the new one written in rust isn't ready to daily yet, hopefully soon though...) hasn't gotten any love in a long time, but I'm surprised you don't see it in Ubuntu. Here's what it looks like for me on Fedora:
Show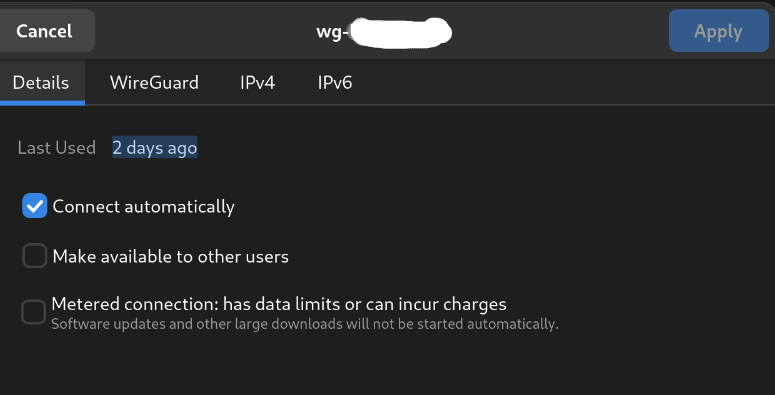
what's weird is I see that on wifi connections but not VPN. On VPN I only get "Make available to other users". Maybe it's the openvpn integration specifically, as opposed to wireguard. I haven't checked ubuntu recently but I don't thiiiink I had it on 18.04/20.04
Oh that could be, I'll set up an openVPN connection later and see if it's any different.
Once again happy with my decision to use Torguard ages ago.
Have you seen their mastodon account?
https://home.speakfree.social/@torguard
Surprised anyone in this instance would use their service since they use their social media account to more or less do NAFO posting.
That's interesting to know about, I guess. I signed up ages ago, on a lifetime $30/yr deal, so they'd have to do something genuinely evil for me to consider some service that's 2-4x the price.
I dont think anything conspiricy brained me quite as much as what happed to the person who leaked the Panama Papers. Not Epstein, not the Jakarta Method, not that time when the FBI and CIA found out every member of the Trot Org they were infiltrating was an informant...
I set up a Wireguard appliance on my VM host a while back but never got around to actually setting my PC up to actually be able to use it or anything
I got letters over a damn textbook when I was in college. I'll need to switch vpns. I need something with port forwarding ideally.
Any body know of any good ones that use wireguard? I have PIA (didn't do anything I needed to be actually secure on fortunately) since I get amazing performance with wire guard vs openvpn, or least it seems to be a lot less picky when the underlying connection is weird or unreliable.
Also, for anyone who needs to hear it, a VPN alone will not protect you and you shouldn't use both at the same time unless you know what you're doing and the security consequences.
I don't think wireguard is recommended yet for privacy reasons, but mullvad has always been solid AFAIK. You can even pay in cash if you like.
The other reply is correct about wireguard and privacy. If you have concerns about the connection to the vpn server being traced back to you, don’t use wireguard.
Wireguard uses perfect forward secrecy, which means that no one can see the private keys and none of your information is ever revealed to a man in the middle. A man in the middle would, though, be able to see that a connection was made between the vpn server and your ip.
It’s worth investigating why that would be a concern and I’ll outline an example here:
You connect your computer to the vpn and go do some stuff. Unbeknownst to you, someone’s been packet sniffing the vpn server you use for along ass time and has accumulated enough information to say for certainty that you were connected right before the stuff was done. Based on recent examples, that’s enough to get a warrant!
How would you mitigate that? Key and server rotation! For example, if you created a wireguard config for a bunch of vpn servers and switched them up from time to time and/or deleted your old config and made a new one with a new key. Easy peasy.
There’s a good overview of some of the problems wireguard can face here. Some of them are shared by other protocols and some are much different than what we’re talking about. Generally though wireguard is very good and almost all concerns are alleviated by key/server rotation.
ExpressVPN also uses dark pattern UI design to make it harder to cancel, if the above wasn't enough of a reason to avoid it.